File detail:
File Name: Micrbarin.exe
MD5: 21AE834BDD5B89BACACCA4D51CF82148
Size: 3.64 MB
NSIS installer file
This file is NSIS installer, we found inside the strings.
Behavioural Analysis
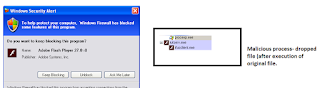
Executed the Micrabarin.exe in the controlled environment to
observe the behaviour. We got new processes comes in the memory and windows
security alert block the process by stating that the file is adobe flash
player. And those new processes are having flash player icon.
Registry traces:
HKEY_CURRENT_USER\Software\TektonIT
HKEY_CURRENT_USER\Software\TektonIT\Remote Manipulator
System
HKEY_CURRENT_USER\Software\TektonIT\Remote Manipulator
System\Server
HKEY_CURRENT_USER\Software\TektonIT\Remote Manipulator
System\Server\Parameters
HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\ShellNoRoam\MUICache
"C:\Documents and Settings\All Users\rutserv.exe" Data: Adobe Flash
Player 27.0 r0
HKEY_USERS\S-1-5-18\Software\Microsoft\Windows\ShellNoRoam\MUICache
"C:\Documents and Settings\All Users\rutserv.exe" Data: Adobe Flash Player 27.0 r0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
"sys"
Data: c:\ProgramData\rutserv.exe
HKEY_CURRENT_USER\Software\TektonIT\Remote Manipulator
System\Server\Parameters "CalendarRecordSettings"
Data: (data too large: 1182 bytes)
HKEY_CURRENT_USER\Software\TektonIT\Remote Manipulator
System\Server\Parameters "FUSClientPath"
Data: C:\Documents and Settings\All Users\rfusclient.exe
HKEY_CURRENT_USER\Software\TektonIT\Remote Manipulator
System\Server\Parameters "InternetId"
Data: (data too large: 352 bytes)
HKEY_CURRENT_USER\Software\TektonIT\Remote Manipulator
System\Server\Parameters "notification"
Data: (data too large: 563 bytes)
HKEY_CURRENT_USER\Software\TektonIT\Remote Manipulator
System\Server\Parameters "Options"
Data: (data too large: 1391 bytes)
HKEY_CURRENT_USER\Software\TektonIT\Remote Manipulator
System\Server\Parameters "Password"
Data: (data too large: 256 bytes)
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List
"C:\Documents and Settings\All Users\rutserv.exe"
Data: C:\Documents and Settings\All
Users\rutserv.exe:*:Enabled:Adobe Flash Player 27.0 r0
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List
"C:\Documents and Settings\All Users\rutserv.exe"
Data: C:\Documents and Settings\All Users\rutserv.exe:*:Enabled:Adobe
Flash Player 27.0 r0
File created
c:\Documents and Settings\All Users\rfusclient.exe
c:\Documents and Settings\All Users\rutserv.exe
Post made by


No comments:
Post a Comment